The regulatory technical standards (RTS) regarding SCA adopted a Commission Delegated Regulation (EU) 2018/389 which will be legally applicable from 14 September 2019. However, it seems that the industry is not ready yet to adopt all the changes. The complexity of the payment industry and the new players in the market may lead to delays. In order to avoid negative consequences, EBA will accept some extends of the deadline in an exceptional way (for example for merchands it is highly probable that it won't be ready on time). The extension will be accepted only if the relevant Conduct Authority has accepted so and follows closely the implementation of the SCA plan during the extended period. The EBA will monitor the consistency of SCA implementation across the EU.
EBA comments on the fact that although : Guidelines on the security of internet payments are applicable since 2015, they are not being applied by all member states. In addition, EBA has published an Opinion on the implementation of RTS on RCA, and a : Single Rulebook Q&A tool.
What is a Strong Customer Authentication (SCA)?
The application of an SCA is based on three elements: the “knowledge”, “possession” and “inherence” element. The elements are independent, in a way that the breach of one does not compromise the reliability of the others and is designed in such a way as to protect the confidentiality of the authentication data.
The inherence element is the most innovative and fastest-moving element. EBA provides in the Opinion a non-exhaustive list of possible inherent elements that includes: retina and iris scanning, fingerprint scanning, vein recognition, face and hand geometry, voice recognition, keystroke dynamics (identifying a user by the way they type and swipe, sometimes referred to as typing and swiping patterns), the angle at which the PSU (Payment Service User) holds the device and the PSU’s heart rate.
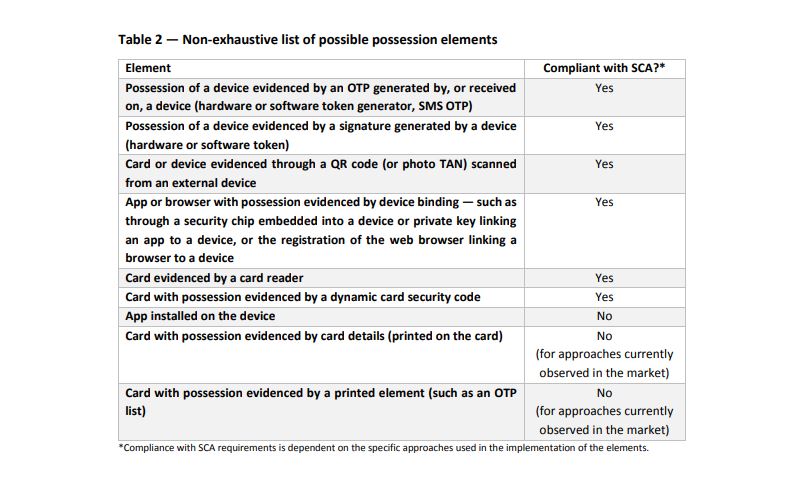
The EBA is of the view that approaches relying on mobile apps, web browsers or the exchange of (public and private) keys may also be evidence of possession, provided that they include a device binding process that ensures a unique connection between the PSU's app, browser or key and the device. Digital signatures and QR codes are also possession elements. The card details and card security code that is printed on the card can constitute neither a knowledge nor a possession element. Only dynamic card codes (codes not written on the card) can be a possession element.
EBA's non-exhaustive list is presented below:
European Banking Authority general comments on SCA
EBA's Opinion provides also some general comments regarding SCA. One point that EBA is stretching already from 2018, is that the two elements required for the SCA should belong to different categories, meaning, for example, one from the knowledge and one from inherence category. Moreover, the independency of the elements is core, in order to provide the highest possible security for the transactions. EBA also points out the possibility of a re-used element for the purpose of an SCA in the same session.The deadline of 14th of September is coming closer and what it is left to see is how prepared the professionals will be and if the EBA's Opinions and Guidelines have been taken into consideration. The project is complex, especially for firms which are not directly subject to PSD2 and they will probably not be ready. The extension given, however, shows flexibility from EBA and Conduct Authorities side.





