The revision of AML detection scenarios is not a straightforward process and could lead to a real AML operational disaster if poorly executed. Experienced industry professionals can help build better detection scenarios that suit your business model, helping to detect, manage and report suspicious transactions more efficiently while lowering the cost of regulatory compliance.
Developing an efficient transaction monitoring system is a multi-step procedure that implies several critical business decisions. The following report won't answer each practical question but hopefully serves as a guide for a better comprehension of transaction monitoring and its implications.
What is AML Transaction Monitoring?

The activity of monitoring financial transactions is part of the ongoing due diligence obligations towards clients and their operations that entities are required to implement in the context of the fight against money laundering and terrorist financing. It is also required by other applicable regulations and security duties: the fight against fraud, tax evasion, computer piracy, etc.
The internal control measures must be efficient and should commensurate with the nature and size of the obliged entities. It means that smaller businesses with fewer means will not be expected to have to have the same resources compared to larger corporates. Smaller businesses should, however, be held responsible for setting the emphasis of their controlling measures where higher risks apply.
How to conduct AML Transaction Monitoring?


In particular, they shall examine, as far as reasonably possible, the background and purpose of any complex and unusually large transactions, as well as any unusual patterns of transactions that have no apparent economic or lawful purpose.
What is a transactional profile?
What is the added value of capturing customers transaction profiles in the fight against money laundering?The capture of a customer's transactional profile can be seen as an enhanced due diligence measure that financial institutions are willing to put forward to frame their knowledge of their customers and their financial operations in the riskiest situations.
Transactional profiles are a summary of a customer's behaviour in his or her interactions with financial institutions and his or her use of the monetary instruments made available during the course of the business relationship with the latter. It can be used to:
- Gain a higher level of accuracy in knowing your customer behaviour and profile
- Alert on deviation of customer behaviour
- Provide an additional layer of information
- Identify abnormal operational usage
- Customer-centric data to refine monitoring tools
- Sharpen customer risk profile
- ...
A customer transactional profile can be built by looking at specific aspects of its transactions, such as what account it uses, what type of financial operations, how much money there is under management, which countries of activities are involved, what are the entering and leaving operations standards, and other detailed information.
Naturally, all transactional information must be classified and related to the type of customer through different criteria, in order to take into account the context of the business relationship and the knowledge of the customer information in the most appropriate way possible.
The reconciliation of this information with the client's actual operations can serve as a basis for evaluation but also for the creation or update of this operational information.
What are AML Transaction Monitoring Solutions?
Ranked by importance, they allow AML and Compliance officers to investigate the associated transaction(s) into the case management system with regard to the specific customer profile and their business relationship.


Otherwise, if the alert is deemed not relevant and discounted, the solution metrics would feed statistical reports to be considered in the course of the detection scenarios (yearly) fine-tuning.
The monitored transactions can be of all kinds, from debit to credit operations, including cash deposits, withdrawals, wire transfers, investments, insurances schemes, national or cross-border transactions, etc.
Centralising the information in a unique solution instead of stand-alone metrics eases the AML analyst's job by providing an in-depth visual context, helping to establish the materiality of the case with detailed information before their eyes.

Do all financial firms require AML Transaction Monitoring solutions?
The answer might appear evident in your case. Still, as a financial firm (credit institution, insurance company, payment institution, electronic money issuer, stockbroking firm, alternative funding platform, …) you might be highly targeted by third-party AML solution vendors. You should focus on the relevance of the tools that your company is willing to invest in.
And if not, are they always necessary or useful?
What if in your business model the onboarding due diligence through your client acceptance is more important than the follow-up of the limited recurrent deposit on a pension savings account restrained in the payment means?
Indeed setting up Detection Scenarios through a third-party transaction monitoring solution can be the cornerstone that will improve your diligence productivity and efficiency. Such solutions can assist you to prevent your business from becoming the favourite channel for criminals to launder their illicit funds.
A significant apprehension, however, that the implementation of AML systems often come with high financial and operational costs.
Whether you decide to internalise or externalise the development of an AML transaction monitoring system, your company will be facing many challenges.
The development phase, the implementation and adjustment with internal systems, the dependencies and the customisation of the detection scenarios are long unavoidable processes that should be taken into account
Although valuable, anti-money laundering transaction scenarios and their monitoring solutions should only be dedicated to financial firms operating in some specific industries and on a particular scale.
Based on your customer population and activity model, billions of operations can occur in a single day. In that perspective, keeping pace with the transaction flow without the aid of a monitoring solution can quickly become unfeasible.

Even by organising the best post-filtering methodology, it becomes laborious to answer your ongoing due diligence obligations and to focus on suspicious cases with sufficient achievement if the amount of transactions to monitor exceeds the million rows of data per day.
Moreover, faster-reaction time is always better-suited when money-laundering and terrorism-financing are at stake. In that aspect, a transaction monitoring solution is significant since it automatically elevates cases to the AML officers and can prioritise actions based on the level of risk considered.
Let’s examine, for instance, the case of a private bank. It can be perfectly able to monitor their customers’ daily operational behaviours without the necessity to invest substantial financial amounts in acquiring the license of an AML transaction monitoring system, resulting in a time-consuming implementation process.
We find that firms that do not face high number of customers or a significant number of regular operations can organise their continuous monitoring measures via humbler methods such as post-filtering data through standard desktop utilities.

After developing a reliable system to capture the operations' information, it would presumably require a medium to advanced analyst to manually sort and filter the extracted data for investigation.
Building a filtering methodology to give consistency to suspicious or riskier cases is a step ahead in improving compliance work productivity and formalising your ongoing due diligence processes towards your customer’s operational behaviours.
Your business could be held responsible for not allocating the means necessary to fight the laundering of illicit money and the misuse of the financial market. Depending on the case, adopting AML monitoring systems is not always required but can become, for companies that generate big data flows, an essential tool for complying with your AML ongoing due diligence obligations.
Why and When should you revise your AML Detection Scenarios?
- continually evolving regulatory landscape;
- evolving trends of criminality;
- sectoral, national and international guidance;
- performance scrutiny;
- special demand from the supervisor;
- ...

Remote business relationships through digital channels are increasing the urgency to adopt real-time identification and verification mechanisms and push forward financial institutions to invest in contemporary technology-driven tools and increase their controlling performance.

It also serves a global harmonisation purpose among the financial actors. Financial firms must take into account and translate these guidelines and technical standards in the face of ML/TF risks that their company is facing.
The performance scrutiny of your transaction monitoring system can also translate into a revision necessity. A wrongly configured system can have a severe negative impact on your AML operational productivity.
Tuning your detection scenarios after conducting an analysis of their performance for both real-time and/or forecast the results in a testing-environment can significantly impact the allocation of your human resources.
Safeguarding analysts interaction solely for the appreciation and validation of relevant alerts will boost the work productivity and improve the detection and mitigation ratios.
By limiting the number of false positives in its transaction monitoring system, a company allows its financial crime officers to focus their investigation skills on concrete risks identified by the system.
Sometimes suspicious transactions are detected and unveil money laundering patterns requiring the financial firms to tackle the situation with fine-tuning corrective actions immediately.
And in case an incident occurs like a query from the FIU on a specific transaction from a customer, do use these examples to interpret if the tool should have escalated it.
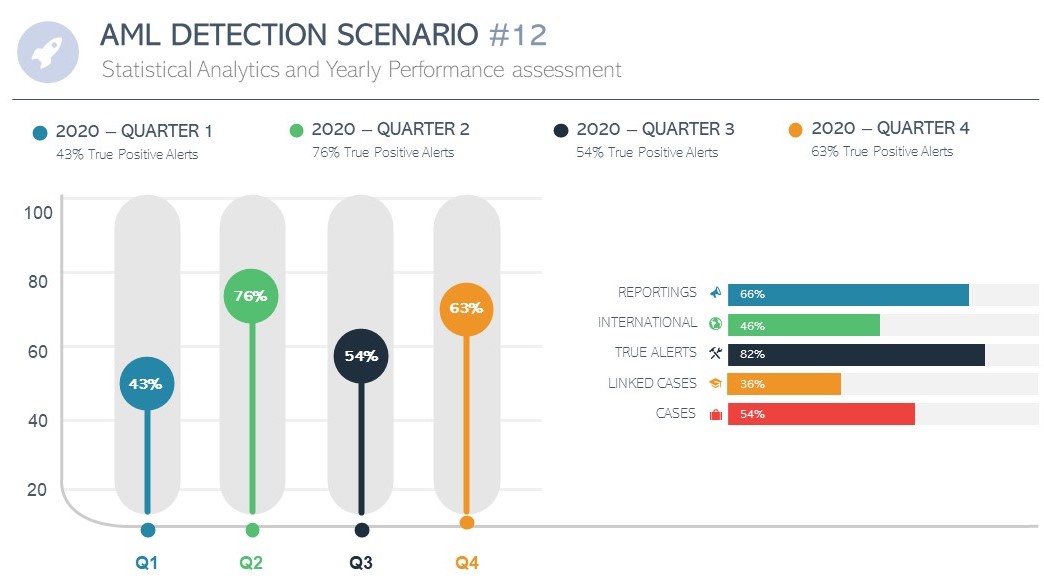
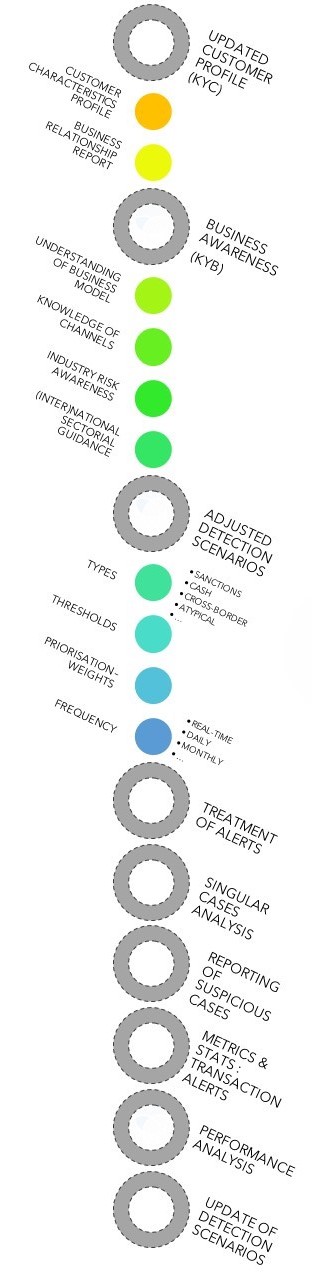
How to Revise, Tune and Improve your AML Detection Scenarios?
Changes should always be tried and analysed in a testing-environment before validation. The adjustments will require to be tested during a substantial period to strengthen the precision of results. Forecasts patterns can also be a reliable indicator if adequately designed.
Creating various versions of a specific scenario and targeting specific distribution channel or products can also foster a risk-based approach in the examination of suspicious cases.

The consequences of a wrong setup in your detection scenario algorithm can have devastating operational consequences leading to the damage of your company’s reputation and severe financial sanctions.
Hence, take no chances when revising or implementing detection rules and surround the developers with qualified industry professionals, financial management and AML manager for stimulating the design of efficient algorithms that consider public guidance, company knowledge and business experience.
Perhaps your company has chosen to rely on a vendor solution that includes a set of standard vigilance scenarios which can become operative only after proper revision and customisation of the settings to suit your business needs. Having the opportunity to adjust the scenario variables directly in the system without the need of the third-party vendor must be considered in this case.
Applying a risk-based approach in the creation of your AML detection rules is essential in complying with your AML obligations and allows to rationalise the allocation of the resources.
Requiring professional assistance from specialists accustomed to the fine-tuning of detection scenarios can stimulate your understanding of your company's money-laundering risk exposure and ensure that all AML regulatory obligations are met.
The baseline of any improvement exercise is to keep track of past performance and define markers. Exploiting data to provide statistical analytics supported by data visualisation reports helps to set in place a risk-based strategy and to classify and prioritise the list of corrective actions.
Changes should always be tried and analysed in a testing-environment before validation. The adjustments will require to be tested during a substantial period to strengthen the precision of results. Forecasts patterns can also be a reliable indicator if adequately designed.
Creating various versions of a specific scenario and targeting specific distribution channel or products can also foster a risk-based approach in the examination of suspicious cases.
Adapting thresholds, considering covering scenario, profiling and deviation scorings are some of the terms you should master to produce efficient aml rules and to elevate your alerts' true positive ratio.
Maintaining a Framework for audit changes is a mandatory condition for the understanding of your transaction monitoring system performance.
Additionally, having the possibility to create whitelists (suppression logic) for safely identified operations while analysing reported alerts, is a valid and commonly used feature that should be used by aml financial crime investigators to help fine-tune the system continuously. Proper maintenance of the list must be ensured.
Transaction monitoring Solutions are brilliant tools that can help your firm tackle fraud, mitigate risks and improve operational control over customer' operations. However, they are part of a much broader context of ongoing vigilance of clients and their financial operations.
- clear management oversight;
- continuous internal training;
- and strong internal policies and procedures that formalise your internal controlling measures.






Great Article! It clearly explains various transaction monitoring detection scenarios. Also, with high risk, new systems are evolved for monitoring transactions.
Dear Charlotte, Many thanks for your support! It is very much appreciated. Every year, the accuracy of automatic detection systems is improved thanks to technological advances (Artificial intelligence - machine learning - cloud platforms, business targeted workflow, ...). By combining the continuous monitoring of existing systems with the new tools available, financial institutions can significantly increase their capture rate of suspicious transactions.
leverages individuals, industrial, public and private sectors, the corporate businesses to fully control, manage and process real-estate assets on the Distributed Ledger and Economy-based Blockchain consensus network. A seamless and fully trusted connection to diverse and disrupt with digital network services.